The matrix below details the areas in cybersecurity where defense contractors and subcontractors should invest in technologies at every level of the value chain to ensure they have unique and watertight cybersecurity products and strategies.
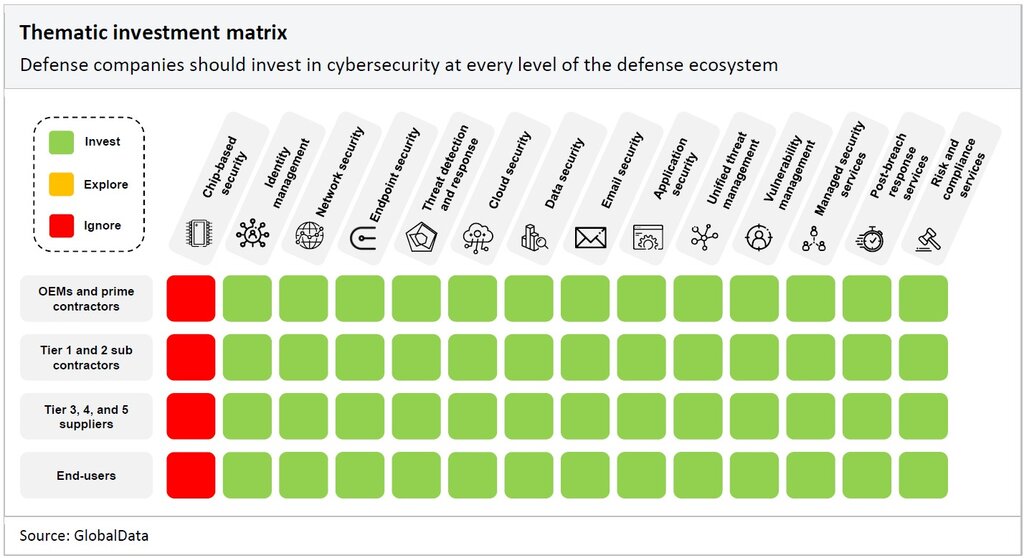
The defense industry should invest in advanced cybersecurity technologies and solutions to protect their networks, systems, and sensitive data. These solutions include implementing robust firewalls, intrusion detection and prevention systems, encryption mechanisms, using AI to enhance analytics and threat detection, and training military personnel to build resilience against future cyberattacks.
Moreover, defense companies should look into collaborating with industry partners and government agencies, as collaboration can enhance cybersecurity posture by sharing information and best practices to help all parties identify emerging threats. Investing in cybersecurity is crucial for defense companies and militaries to protect critical national infrastructure, preventing hostile actors from gaining control of sensitive information and safeguarding national security.
Consequently, investing in cybersecurity capabilities is fundamental in gaining an advantage against their adversaries and preventing hostile actors from accessing defense data and weapon information.
How does digitalization accelerate the need for cybersecurity?
Digitized defense systems are targets for hostile actors seeking to gain access to sensitive data and disrupt communication. For example, Ukraine’s foreign cyber defender, Team OneFist, stole sensitive data from Russian military firms worth $1.5 billion and hacked equipment such as cameras to spy on Russian troops.
Cybersecurity practices can help defend computers, servers, mobile devices, networks, and data from malicious attacks. For example, defense companies and militaries that use firewall solutions will protect their computers or networks from unwanted traffic. A firewall can monitor and control unwanted traffic between an internal network (trusted to be secure) and an external network (not trusted). It can then block unauthorized access to the network and determine the identity of potential attackers.
How does big data impact cybersecurity?
The healthcare and pharmaceutical industries are key targets of malicious cyber threat actors due to the vast amount of valuable and sensitive data and IP they hold. Therefore, it is vital for life sciences companies to protect these assets. As the industry becomes more digitalized, cybercriminals have more avenues to steal personal and proprietary data, including from medical health records and connected medical devices.
Connected devices that collect personal health data, such as wearables, frequently exchange data with paired devices via Bluetooth, which makes them especially susceptible to hacking. Furthermore, individual devices that contain personal health information generally have little cyber protection and are often not connected to managed networks. Individual devices would benefit from implementing cybersecurity software like network security, vulnerability management, and identity management.
How does the data deluge accelerate the need for cybersecurity?
The increasing data streams that comprise the OODA loop means more connected devices must be cyber-secure. The director of operational test and evaluation in the US Department of Defense confirmed that “almost every weapon in the warfighter’s arsenal is software-defined, and we are more likely to improve system lethality by installing new software than by modifying hardware.”
However, each software update can come with its own cybersecurity risk. Data in any format has always been a key discriminator on the battlefield, providing valuable information that can be processed and turned into an actionable output for front-line users. However, as the OODA loop increasingly relies on complex strategy and planning, any data breach would be a significant intelligence coup by an enemy force.
Widespread data collection also means companies and military institutions increasingly outsource their data management. This will accelerate the need for cybersecurity as bad actors prefer to target smaller suppliers to the largest defense contractors rather than attempting to attack larger companies that can afford to spend more on cybersecurity.
Another area where cybersecurity will play an important role is in the unmanned systems sector. The increased use of unmanned systems will require additional investments in cybersecurity due to their vulnerabilities. Unmanned vehicles are part of the broader IoT ecosystem, and the interconnected nature of IoT systems increases the risk of hacking and cyberattacks. Controlling them is a process that includes data being received and sent to and from a control station, often using satellite telecommunications.
In some cases, these systems must operate in areas with no signal (e.g., mountains, under the water) and rely on their onboard computers to continue the mission. Therefore, securing them against cyberattacks is critical, not only for the information they possess but also for the fact that a growing number of platforms are armed with lethal weapons systems, which could be used against allied forces should a hostile entity gain control over the unmanned platform’s command and control functions.
How does the complexity of IoT accelerate the need for cybersecurity?
The modern soldier has become more connected, and militaries are now more reliant on IoT. This makes securing IoT devices against cybersecurity threats a major imperative. According to Ron Stefanski, business professor at Cambridge College, “the expansion of interconnected devices that come with IoT also widens the threat surface for potential cyberattacks… therefore imperative that ADS companies implement robust security safeguards to fortify their evolving technological ecosystem.”
Conducting a thorough investigation of cybersecurity risks and investing in anti-malware software will identify potential vulnerabilities in computer systems and networks. Defense companies can then develop strategies to mitigate those risks. For example, Israeli agencies reportedly use the Pegasus software to spy on Hamas’ mobile communications. Pegasus is a ‘zero-click’ malware that is placed onto a target’s communication device and activated without them knowing or needing to click any links, giving the attacker access to the target’s entire mobile device and data.
5G networks enhance real-time command and control (C2) on the battlefield by providing connectivity to technologies such as AI, unmanned systems, and cloud networking. For example, 5G-enabled AI applications can process information much faster and analyze data more efficiently.
Implementing monitoring systems and threat detection mechanisms can help defense companies and militaries identify and mitigate potential cyberattacks. Incorporating specialized AI tools that can automate threat and vulnerability detection using predictive data modeling to analyze network behavior will further increase defensive cyber capabilities.
How does AI adoption accelerate the need for cybersecurity?
AI is a tool for both protecting against cyberattacks and launching them. AI can accelerate malware, allowing code to change constantly, thus making it more difficult to detect. More sophisticated AI techniques could enable hackers to bypass facial security and spam filters, produce fake voice commands, and avoid anomaly detection engines. New autonomous technologies can also be used for offensive cyber operations, which involve identifying and exploiting vulnerabilities in the infrastructure of a hostile entity. This strategy aims to gain an advantage over the enemy by using their weakness in cyberspace. Offensive cyber operations encompass activities like hacking and data breaches. However, it is important to note that these operations can also contribute to enhancing the cybersecurity of allies, thereby ensuring their safety and readiness.
The US DoD has developed a strategy for offensive cyber operations that focuses on protecting the cyber domain in collaboration with allies and partners. The objective is to support the development of their cyber capabilities, enhancing the potential for future cyber cooperation. By working together, allies can enhance their collective cybersecurity posture and effectively defend against cyber threats.
An AI-enabled defensive approach allows cyber forces to stay ahead of the threat as machine learning (ML) technology improves the speed and efficacy of threat detection and countermeasures. ML solutions can boost threat detection accuracy and authorize instant autonomous responses to react to new AI-generated cyberattacks. Innovations such as ML, AI-enabled malware, and cloud technology are expected to enable a more proactive approach to cybersecurity. Furthermore, by training cybersecurity professionals in the latest techniques and technologies, they can gain an understanding and identify AI-led attacks.
Training includes learning to recognize patterns and behaviors that indicate malicious intent and using AI tools and algorithms to analyze data for potential threat signatures. As a result, defense companies and militaries can better identify and mitigate cyberattacks before they cause damage to the industry’s reputation or security. Consequently, cybersecurity professionals are essential to protect defense systems and data and enhance military readiness and capabilities in the face of emerging AI-based cyber threats.
How does hybrid warfare accelerate the need for cybersecurity?
Geopolitical tensions between countries can result in cyberattacks as a means of retaliation or gaining a strategic advantage. Countries with strained political relations often target each other’s military, financial, and infrastructure capabilities with cyberattacks.
These attacks are becoming more aggressive and a threat to national security due to their ability to disrupt and damage defense companies' reputations and obtain classified information. For example, Lockheed Martin was targeted with a ransomware attack in 2022 by Killnet – a pro-Russian group that specializes in denial of service (DoS) and distributed denial-of-service (DDoS) attacks – and claimed to have extracted personnel identification data of Lockheed Martin’s employees.
Since the Russian invasion of Ukraine in February 2022, the frequency of cyberattacks against Ukrainian targets has increased, with repercussions felt across Europe and beyond. The CyberPeace Institute reports that in May 2023, there were 1,998 cyberattacks against Ukraine, with operations conducted by 98 different actors. These incidents targeted 23 critical sectors, including finance and healthcare, and extended to 49 other countries, such as the UK, Germany, France, Switzerland, and the US.
Implementing cybersecurity solutions and practices such as the European Parliament’s Common Security and Defense Policy (CSDP), an integral part of the EU’s foreign and security policy, will enable military forces to enhance capabilities in peace-keeping operations and conflict prevention while strengthening international security. According to a 2023 report by the European Parliament, CSDP is a “key pillar of the EU Strategic Compass towards strengthening security and defense policy.”
Implementing the CSDP will support the strategy for enhancing the resilience of the security sector, including cybersecurity, countering disinformation, and other coordinated information operations.
On May 7th, 2024, the UK’s Ministry of Defense (MoD) suffered a suspected Chinese cyberattack that exposed the personal details of tens of thousands of UK military personnel. The cyberattack targeted the MoD’s payroll system, including names and bank details of current and former armed forces members.
The consequences of failing to invest in cybersecurity measures can be severe and wide-ranging, damaging the defense industry’s finances and reputation, increasing concern over the potential loss of control over military weapons and equipment, disrupting supply chains, and leading to severe legal or regulatory consequences.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.