Unencrypted communications by Russia undermines operational security in Ukraine
Despite the Russian military’s familiarity with this threat, there have been multiple high-profile instances of Russian forces being eliminated, according to GlobalData.
As the war in Ukraine nears its twelfth consecutive month, the recent high casualty strike conducted on New Year’s Day by the Armed Forces of Ukraine (AFU) against a Russian base in Makiivka has highlighted the importance of Operational Security (OpSec).
Following this attack both official and unofficial sources including the Russian Ministry of Defence (MoD) claimed that Russian units were identified and targeted due to their use of unencrypted mobile phones. Should this be proven true, it would not be the first time that the AFU have exploited the lack of OpSec within the Russian military and highlights an increasingly endemic threat to the Russian operations.
The use of cellular phone signals to identify enemy positions is by no means a new tactic in modern conflicts. Both the US and UK military employed mobile phone tracking software installed aboard modified King Air 350ER special mission aircraft to locate and identify high value targets during counter-terrorism operations against Al-Qaeda and ISIS. Western strategists and their international counterparts have repeatedly highlighted the risks posed by servicemembers’ personal mobile devices, with numerous NATO forces having implemented stringent OpSec procedures during deployments to mitigate this threat.
Russian military strategists are also acutely aware of this risk, having employed electronic warfare (EW) to good effect during the ‘cold’ stages of the war between 2014-2022 and to some extent during the ongoing invasion of Ukraine to track AFU troop movements. The Russian military has also experienced several OpSec failures in recent years during operations in Syria and during domestic exercises, with social media posts by Russian soldiers having been used to geolocate troops, identify sensitive equipment and even bring criminal accusations against the Russian state, as was illustrated by the inquiry into the shooting down of commercial airliner MH17.
Yet despite the Russian military’s familiarity with this threat, there have been multiple high-profile instances of Russian forces including high ranking officers being identified, targetted and eliminated due to their frequent use of unsecured cellular communications, leaving observers to question, why Russian military forces have remained unable to mitigate this strategic threat?
The primary reason for this failure revolves around the inherent inadequacies of Russian military hierarchy and leadership when it comes to forming a unified and disciplined fighting force. Reports over the last several years have highlighted the endemic corruption and nepotism which have plagued Russian military command, with inadequate training and poor leadership been further exacerbated by the absence of a dedicated cadre of non-commissioned officers (NCO) throughout the services.
This has resulted in a widespread lack of tactical discipline amongst Russian servicemembers, with the use of unsecured mobile phones and the dissemination of sensitive information proliferating as a direct consequence of these failures. Since Russian forces first annexed Crimea and infiltrated the Donbass in 2014, civilian analysts from prominent institutions such as RUSI and Bellingcat have relied on open-source intelligence (OSINT) to verify the presence of Russian military units in Ukraine using images and social media posts published by Russian soldiers.
Russian reaction to mobile phone usage
The Russian MoD responded to this issue by confiscating the mobile phones of Russian forces prior to their deployment to the Ukrainian theatre in February 2022. However, the Russian high command’s failure to communicate critical intelligence to frontline units led to a further breakdown in discipline, with countless documented instances of Russian forces confiscating mobile phones from Ukrainian civilians, often with lethal force, to acquire communications capabilities and regain some degree of situational awareness.
The consequences of this inadequate hierarchical structure and leadership are even more pronounced amongst the Russian proxy forces, with the less disciplined militias of the Donetsk People’s Republic (DPR) or the Luhansk People’s Republic (LNR), seemingly incapable of maintaining OpSec throughout the conflict. This resulted in several critical strikes against large concentrations of DPR and LNR forces in the summer of 2022, while the main operations base of the Russian Wagner private military corporation in Popasna was destroyed by a strike in August 2022 after images posted online allowed the AFU to pinpoint its location. That strike was notable as it didn’t involve any interception of communications by the AFU’s EW units, but rather a simple yet costly failure in OpSec by Russian forces.
This disparity in professionalism and expertise has only been further compounded in recent months by the Russian military’s conscription drive and Wagner’s recruitment efforts from prison populations, both of which are resulting in poorly disciplined fighters being deployed en-masse to the Ukrainian frontline in a desperate effort to offset mounting Russian casualties.
In addition to the failure of Russian military leadership and discipline, the lack of a viable encrypted communications solution has meant that even the most disciplined elements of the Russian armed forces are in many cases obligated to use mobile phones and other unsecured devices throughout the conflict. The Russian military does possess a military cryptophone system known as ‘ERA’, which would theoretically allow Russian forces to communicate securely in theatre using specialised encrypted radios and terminals.
However, the ERA system was designed to rely on existing communications and cellular networking infrastructure, which was heavily disabled by Russian strikes in the early days of the war. After Russia targeted numerous 3G/4G LTE antennas and masts in a bid to undermine Ukrainian communication capabilities, the lack of cellular broadband coverage also left their own forces unable to communicate securely.
This strategic mistake proved extremely costly during the opening months of the conflict, with US officials having confirmed in March 2022 that high ranking Russian military officers had been targeted and killed by precision artillery strikes after the AFU (and possibly its US ally) had identified their exact positions using EW capabilities to intercept unencrypted radio and mobile phone communications.
The immediate impact of this mistake was further exacerbated by the additional failures of Russian military logistics. Though Russian forces were aware of the threat posed by the lack of encrypted communications, the endemic corruption within the Russian military coupled with the sanctions imposed on the domestic defence industry prevented the Russian MoD from supplying their forces with sufficiently advanced alternatives.
Seeking solutions from China
There is evidence that in March 2022, Russian units were being issued commercial analogue radios manufactured by Chinese firm BaoFeng, which were unencrypted and provided less varied functionality than commercial smartphones. This incentivised the use of personal mobiles during the opening months of the war, while continued sanctions and logistical ineptitude has meant that some Russian forces continue to communicate using such methods out of necessity.
One of the most striking consequences of the Russian military’s OpSec failures in Ukraine is that civilians within and beyond Ukraine are assisting the AFU in identifying Russian troop movements, in some cases even providing targeting data using OSINT gathered online. Throughout the conflict, the AFU has relied on a loose network of partisan supporters operating behind enemy lines to assist them in acquiring and verifying critical intelligence, with the Ukrainian intelligence services having fielded smartphone applications designed to assist civilians in geolocating Russian military equipment.
The prominent use of OSINT against Russian forces has further strategic impacts beyond the battlefield, as international observers are exploiting these OpSec failures to collect evidence of war crimes and counteract Russian political narratives in order to undermine the Russian government’s international credibility.
It is worth noting that despite the significant material support the AFU has received from its western allies, they too still rely on conscripted soldiers with limited training and remain unable to supply encrypted communications solutions to all of their forces. This has meant that many AFU units such as the Territorial Defence Forces and the Foreign Legion to rely on personal mobile phones to communicate on the battlefield, while many also post combat footage and images to social media.
Nevertheless, the AFU has made a concerted effort to standardise OpSec practices and instill communications discipline through coherent training and leadership. As long as the Russian armed forces fail to replicate the AFU’s successes, they will remain at an almost fatal strategic disadvantage for the remainder of the conflict.
It’s clear that the platform technologies and applications that are underpinning online gaming and the metaverse are the very same that will usher in the next level of military superiority
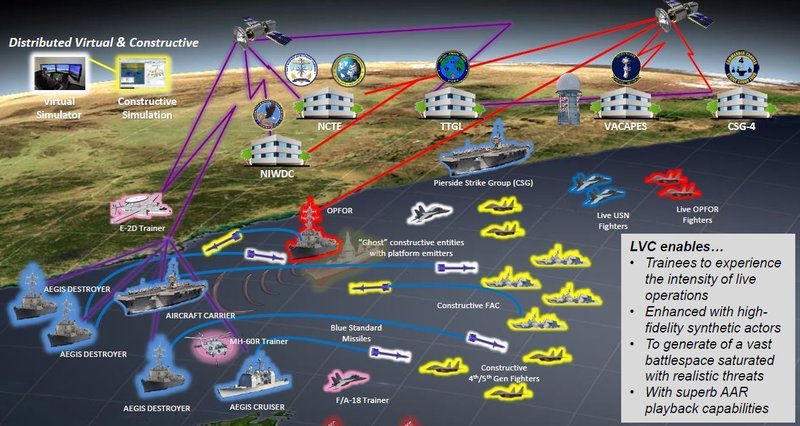
// The US Navy’s Continuous Training Environment enables live virtual constructive training with live and synthetic systems around the globe. Credit: Ron Keter
// Main image: Russian forces have struggled to maintain effective encrypted communications on the battlefields of Ukraine. Credit: Vitaly V Kuzmin.
UKRAINE WAR